Not that long ago, few companies even considered purchasing insurance to mitigate their financial exposure from a cyber incident, and for those that did, obtaining a policy was as easy as filling out an application and writing a check. Those days are now squarely in the rearview mirror. Today, companies everywhere are rushing to get cyber insurance — the value of the global cyber insurance market reached $13.33 billion in 2022 and is projected to soar to $84.62 billion by 2030.
However, the increased number of policies combined with the sharp uptick in costly attacks led to higher costs for cybersecurity insurance providers. To stem their losses, insurance companies now often require proof that an organization has implemented a variety of security measures in order to be eligible to purchase a policy.
Rather than resisting or resenting risk assessments from potential cyber insurance vendors, IT leaders should regard them as an opportunity to strengthen their organization’s security posture.
Cyber insurance involves risk assessment
Across the insurance industry, policy requirements and premiums vary according to risk assessment. For instance, installing an anti-theft system might reduce the cost of insuring an expensive sports car. A person living in a flood plain can expect to pay more for a homeowner’s policy than someone with a similar house on higher ground — or they might not be able to purchase a policy at all, as homeowners in states like Florida are discovering.
It is the same for cyber insurance. An insurance provider may impose more security demands on a company that hosts large volumes of personally identifiable information (PII) than it does for a company of similar size with far less PII. And organizations that lack sufficient security controls to bring risk down to a level acceptable to an insurance provider might not be eligible for any policy at any price.
What cyber insurance actually covers
The main focus of cyber insurance is obviously on covering the financial risks of an incident. Typically, you can expect the insurance to cover the firsthand costs to the business that are the direct result of the cyber event, such as:
- Forensic analysis and incident response. Some insurers require that you engage specific managed incident response services.
- Recovery of data and systems caused by actual loss and destruction.
- Cost of the downtime due to the cyber event.
- Costs incurred from sensitive data breaches, such as handling PR activities, notifying impacted clients, or even providing credit monitoring services to customers.
- Legal services and certain types of liability for regulated data, including covering the costs of the civil lawsuits.
It is important to note that insurance rarely or never covers some of the longer-lasting impacts of the event, such as any future profit loss due to theft of intellectual property or the need to invest in cybersecurity program improvements after the event.
There is no consensus on reimbursement for paying a ransom. Not all insurers cover this type of expense. Some experts argue that it can encourage further attacks and fund criminal activities. In some jurisdictions, the discussion is going back and forth on whether paying ransom should be banned altogether.
As with any insurance policy, you can expect extra clauses. These may include the top amount they cover, the requirement to go through a due process with the law enforcement agencies, or involvement in professional ransom-negotiation services.
The must-have security measures for cyber insurance
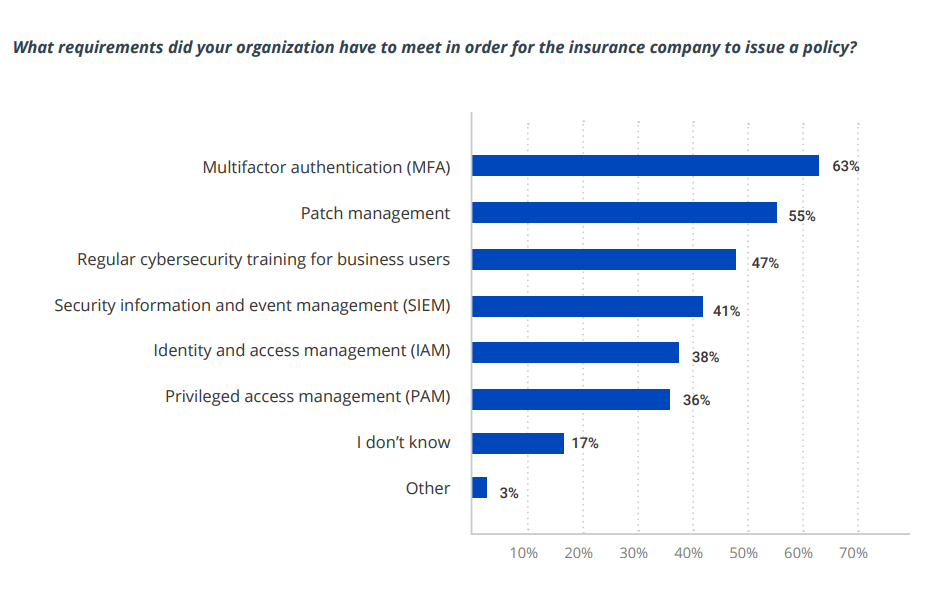
A recent Netwrix study reveals useful details about the process of qualifying for cyber insurance today. It found that 50% of organizations with cyber insurance implemented additional security measures either to meet the requirements of the policy they selected or to simply be eligible for a policy at all. The figure below shows the specific requirements they reported having to meet:

Image Credits: Netwrix/Netwrix Hybrid Trends Security Report 2023
Don’t take this list as comprehensive or authoritative. For instance, implementing MFA does not necessarily mean requiring MFA for all users; an insurer might require additional authentication only for users with privileged access to sensitive data and systems. In addition, remember that these controls are interrelated. For example, in order to require MFA for access to particular types of data, you need to know where sensitive and regulated data resides and have control over user and administrative privileges.
https://techcrunch.com/2023/07/28/cyber-insurance-audit-painful-necessity-or-a-valuable-opportunity/