- Hackers were recently spotted abusing a flaw in multiple Cleo software tools
- Cl0p ransomware gang took responsibility for the attack
- The group has started listing victims on its website
The prolific ransomware threat actor Cl0p has added partial names of some of the companies that were successfully targeted through bugs in Cleo software. This is likely part of its pressure tactic, as it tries to extort money from its victims.
In early December this year, news broke that multiple managed file transfer tools from the same developer called Cleo Software were being abused to launch attacks and possibly steal data. At the time, cybersecurity researchers at Huntress claimed LexiCom, VLTransfer, and Harmony were all vulnerable to CVE-2024-50623, an unrestricted file upload and download vulnerability that could lead to remote code execution.
Cleo allegedly released a patch in October which didn’t entirely fix the issue, leaving the doors open to hackers. Huntress, alone, said it observed at least 24 victims. At the time, the researchers could not attribute the attack to any specific group, since the evidence was inconclusive, but it wasn’t long before Cl0p came forward to claim responsibility.
Listing victims
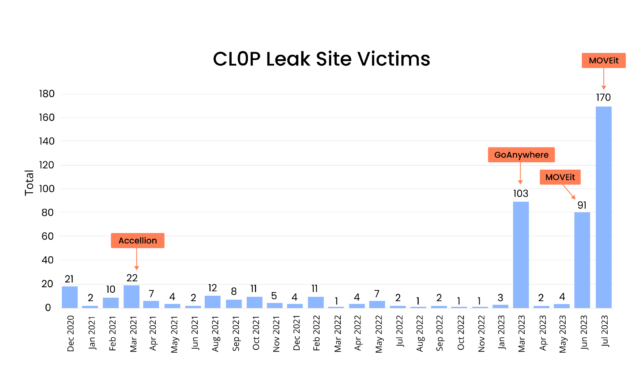
For those unaware, Cl0p is a threat actor best known for exploiting flaws in MOVEit, another managed file transfer tool. This attack resulted in thousands of breached organizations, and sensitive data on millions of people being stolen.
Now, TechCrunch reported that the group took credit for stealing data from at least 66 companies, as it listed their partial names on their website. The gang apparently said it would soon reveal full names of their victims.
“Victim organizations so far have included various consumer product companies, logistics and shipping organizations, and food suppliers,” Huntress said at the time.
Soon after Huntress’ announcement, the US Cybersecurity and Infrastructure Security Agency (CISA) added the Cleo bug to its Known Exploited Vulnerabilities (KEV) catalog, confirming the findings and giving federal agencies three weeks to patch up or stop using the tools entirely.
Via TechCrunch
You might also like
- Cl0p ransomware group says it was behind Cleo attacks
- Here’s a list of the best antivirus tools on offer
- These are the best endpoint protection tools right now
https://www.techradar.com/pro/security/clop-ransomware-lists-cleo-cyberattack-victims


Leave a Reply