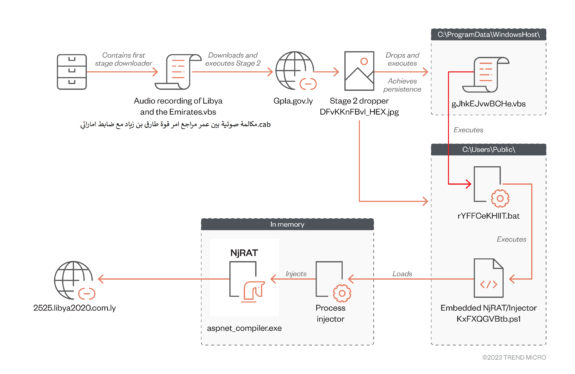
New Research Delves into the World of Malicious LNK Files and Hackers Behind Them
Cybercriminals are increasingly leveraging malicious LNK files as an initial access method to download and execute payloads such as Bumblebee, IcedID, and Qakbot. A recent study by cybersecurity experts has shown that it is possible to identify relatio…